What rock was large enough that I somehow was unaware of this book's existence the last 20 years of my life?
I just finished reading The Cuckoo's Egg: Tracking a Spy Through the Maze of Computer Espionage by Cliff Stoll. The book is based on the true account of Cliff Stoll's experience tracking a hacker through a laboratory computer network at Berkeley in the mid 1980's. The author quickly finds himself in a year long obsession that involved military targets, several US government agencies, and law enforcement from multiple continents.
The story completely sucked me in. The amazing part is more than 25 years later, with the exception of bandwidth and the shear number of targets, not much has really changed. Detective book fans will enjoy it. Security geeks will love it. Incident Responders should be required to read it.
Thursday, December 23, 2010
Not Just Another Analysis of Scareware
Introduction to our Sample
The initial infection came to my attention from an end user. He had reported all Google searches from his browser seemed to be forwarding to hxxp://findgala.com and he was getting warnings about malware on his computer. The system infected was a reasonably up to date Windows 7 notebook. The system was missing the latest patch for Adobe Flash (v 10.1.102.64). The user did not have administrator privileges, the windows firewall was enabled, Internet Explorer 8 with the default of medium/high security was set for the Internet Zone, and Symantec Endpoint 11.X was installed with up to date definition files. Note that Windows UAC was NOT enabled.
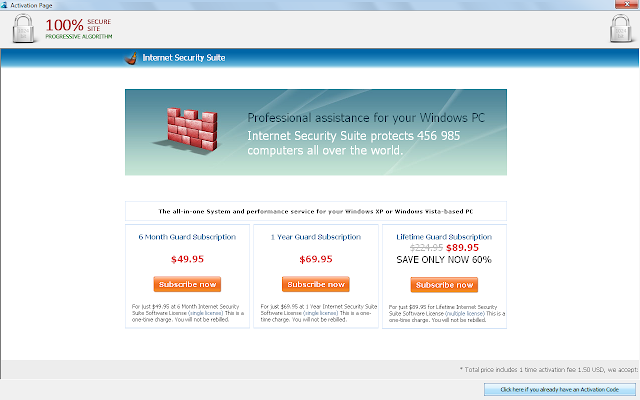
A quick assessment of the system determined it had been infected with some form of scareware. All existing desktop shortcuts had been removed and two shortcuts named "Computer" and "Internet Security Suite" remained. These pointed to "C:\ProgramData\891b6\ISe6d_2229.exe /z" and "C:\ProgramData\e6db66\ISe6d_2229.exe /hkd" respectively. The folder containing the executable was marked hidden and I noted the process was running via TACKIST /SVC. An icon running in the system tray when accessed presented the following screen.
Symantec Endpoint Protection seemed to be neutered by the infection as did several other Windows tools including Task Manager. Initial searching on the internet for the title of the malware only pulled links to legitimate Anti Malware products including CA, Zone Alarm, and Verizon's Internet Security Suite service.Virus Total returned the following analysis. Here is a summary of the file submitted:
Static Analysis
I began with static analysis of the file system by mounting the image with FTK Imager Lite. I exported the Master File Table and parsed it with analyzeMFT . With the estimated time of infection obtained from the victim I was able to pinpoint the file's created and modified during the initial infection.

The initial few files listed in the MFT caught my attention first.
I moved on to use the MFT to locate all files associated with the infection and export the hashes. Here is a summary files found in the /[root]/ProgramData folder:
There were also strings associated with a Microsoft Windows manifest file. Such a file can be embedded in software by the developer to instruct Windows Vista and Windows 7 on what Privileges the software needs to run as. The default setting of "run as the user" was obtained from the strings:
Dynamic Analysis
I began dynamic analysis by first attempting to infect a virtualized Windows 7 system in my lab (Note: all initial attempts were with administrator privileges with UAC disabled). Running the executable seemed to generate a runtime error, so I attempted to run it from the command prompt with the /hkd switch found in the desktop shortcut during static analysis. Process Monitor was used in an attempt to capture all file, registry, and network connection changes during infection. The following error was displayed;
Thinking it picked up on Process Monitor, I tried again but without procmon.exe but I was presented with the same error. It seemed that this sample was VM aware. Again I attempted to infect a clean install of Windows 7 on physical hardware with procmon.exe and again, I was met with failure. I turned to utilizing CaptureBat to monitor file and registry changes during install. Infection proceeded but I noted my sample used for analysis had been removed. On further inspection, it appeared that a .bat file was the culprit. The contents of the file were as follows;
Please note, no attempt was made to identify these files as legitimate malware by myself, although that may be an interesting exercise for another time. Not unlike an episode of the Soprano's, the victim is intimidated into buying protection and is offered several opportunities to buy a subscription. Multiple subscription options are available.
At one point my lab system spewed a blood curdling scream from its speakers before displaying yet another option to "protect" oneself (a little over the top if you ask me). My favorite feature goes to Chat Support however.
I do not think Jane appreciated my bluntness. Network connections for both the subscription service and chat support sessions were collected with the following script which leverages the netstat command.
Soon after this behavor was noted. The executable associated with the infection was mysteriously removed from the system. Attempts to duplicate this behavior later failed.
Further analysis of the infection and sample was done without administrator rights and with UAC disabled. No edit of the hosts file or registry keys in HKLM were noted, however. The malware still setup shop within the ProgramData and User Profile locations noted with the earlier analysis but the fact the user with the original infection had no administrator rights and the host file and HKLM keys were modified remains a bit of a mystery. One might speculate, the original payload might behave differently.
Further Google searching utilizing these findings led me to Microsoft's Malware Protecton Center write-up on Rogue:Win32/FakeVimes. Although Virus Total had not indicated such, it would seem our sample has had many aliases and upgrades.
Lessons Learned
All in all I learned a lot and had fun analyzing the sample (it beats watching sitcoms). Few things I noted for future analysis attempts.
Feel free to ping me if you would like a copy of the sample. I would be more than happy to trade notes with others.
Update: Questions Unanswered
Updated on December 30, 2010.
Curt Wilson was kind enough to comment on my analysis earlier this week. He brought up an interesting tidbit that I had missed. The title of error message displayed when attempting to perform dynamic analysis in a virtualized environment references Themida, a known packer used in malware. The following screen shot obtained from Google images is telling:
According to the results of my initial Google searches, Themida has been around for some time. There are some scripts available for OllyDbg to unpack executables using this tech so I hope to continue down the rabbit hole.
Moreover, I think the files placed in the recent folder of the user profile is worth a quick look, as is the payloads of packet captures. Looks like I have some interesting commutes ahead of me on the train. Until Part II of the analysis, Happy Hunting!
The initial infection came to my attention from an end user. He had reported all Google searches from his browser seemed to be forwarding to hxxp://findgala.com and he was getting warnings about malware on his computer. The system infected was a reasonably up to date Windows 7 notebook. The system was missing the latest patch for Adobe Flash (v 10.1.102.64). The user did not have administrator privileges, the windows firewall was enabled, Internet Explorer 8 with the default of medium/high security was set for the Internet Zone, and Symantec Endpoint 11.X was installed with up to date definition files. Note that Windows UAC was NOT enabled.
A quick assessment of the system determined it had been infected with some form of scareware. All existing desktop shortcuts had been removed and two shortcuts named "Computer" and "Internet Security Suite" remained. These pointed to "C:\ProgramData\891b6\ISe6d_2229.exe /z" and "C:\ProgramData\e6db66\ISe6d_2229.exe /hkd" respectively. The folder containing the executable was marked hidden and I noted the process was running via TACKIST /SVC. An icon running in the system tray when accessed presented the following screen.
Symantec Endpoint Protection seemed to be neutered by the infection as did several other Windows tools including Task Manager. Initial searching on the internet for the title of the malware only pulled links to legitimate Anti Malware products including CA, Zone Alarm, and Verizon's Internet Security Suite service.Virus Total returned the following analysis. Here is a summary of the file submitted:
File Name: ISe6d_2229.exeMy general impression of the GUI was this was a well designed piece of code. I imaged the system with dd and instructed the desktop engineers to wipe the system and reset all the user passwords. This proved to be a mistake on my part as I did not verify my image before they wiped the system. Later I found myself unable to boot the raw image in VMware after converting it to a VMDK with Raw2VMDK (blue screen on loading the OS).
File Type: Windows 32 bit Portable Executable
MD5: 699ebebcac9aaeff67bee94571e373a1
SHA1: ed763d1bc340db5b4848eeaa6491b7d58606ade2
File size: 3590656 bytes
First seen: 2010-11-14 01:20:29
Last seen: 2010-11-16 15:52:22
Static Analysis
I began with static analysis of the file system by mounting the image with FTK Imager Lite. I exported the Master File Table and parsed it with analyzeMFT . With the estimated time of infection obtained from the victim I was able to pinpoint the file's created and modified during the initial infection.

The initial few files listed in the MFT caught my attention first.
The two prefetch files should give a hint of the name and location of the payload. I use Prefetch Parser to parse the C:\Windows\Prefetch folder to obtain some more details:
Record Type Parent Filename 63861 Folder 602 e6db66 63915 File 2755 TASKKILL.EXE-8F5B2253.pf 63926 File 2755 SETUP_2229[1].EXE-11C68EE8.pf 63923 File 63861 ISe6d_2229.exe
Further analysis of the .pf files gave me the location and names.
Record File Times Run UTC Time SETUP_2229[1].EXE-11C68EE8.pf SETUP_2229[1].EXE 1 Sat Nov 13 01:16:53 2010 TASKKILL.EXE-8F5B2253.pf TASKKILL.EXE 1 Sat Nov 13 01:16:53 2010 RUNDLL32.EXE-80EAA685.pf RUNDLL32.EXE 1 Sat Nov 13 01:17:16 2010
SETUP_2229[1].EXE-11C68EE8.pfIt does appear the sample originated from the web. Unfortunately, I could not locate SETUP_2229[1].EXE or ANPRICE=85[1].HTM in the image. Most likely overwritten after several days of use post infection, I moved on the parsing the Internet browser history by using MiTeC Windows File Analyzer and began parsing the last few web sites and searches completed by the user. Unsuccessful in locating the source of the payload, I was not able to verify if it was delivered via a vulnerability or user interaction.
\USERS\%USERNAME%\APPDATA\LOCAL\MICROSOFT\WINDOWS\TEMPORARY INTERNET FILES\CONTENT.IE5\G4KYBRHH\SETUP_2229[1].EXE
TASKKILL.EXE-8F5B2253.pf
\USERS\%USERNAME%\APPDATA\LOCAL\MICROSOFT\WINDOWS\TEMPORARY INTERNET FILES\CONTENT.IE5\G4KYBRHH\ANPRICE=85[1].HTM
RUNDLL32.EXE-80EAA685.pf
\PROGRAMDATA\E6DB66\ISE6D_2229.EXE
I moved on to use the MFT to locate all files associated with the infection and export the hashes. Here is a summary files found in the /[root]/ProgramData folder:
The following summarizes files found in the /[root]/users/%username%/ folder:
MD5 File cd407baa9a55b9c303f0c184a68acc5c \E6DB66\6139ba67beb5a1febb1e8cfc73a42e9c.ocx 699ebebcac9aaeff67bee94571e373a1 \E6DB66\ISE6D_2229.EXE 2e317d604f25e03b8e8448c6884f64e3 \E6DB66\ISS.ico 3ee5ee57af2f62a47d2e93e9346b950f \E6DB66\mcp.ico be44f801f25678e1ffdd12600f1c0bc7 \ISKPQQMS\ISXPLLS.cfg
I also noted that the hosts file had been modified at the time of infection. The following is a sample of entries that had been added (note: additional countries root domain entries for the top search engines were also added but are not included in this analysis for simplicity's sake):
MD5 File 2b7509a2221174a82f6a886bbdd2e115 \Desktop\Computer.lnk fb16300f2f9799376807b13ad8314ca2 \Desktop\Internet Security Suite.lnk fd00cfeecc333aedc56fd428f2b9b5ba \AppData\Roaming\Internet Security Suite\Instructions.ini 4635f17db7d2f51651bebe61ba2f4537 \AppData\Roaming\Microsoft\Windows\Recent\ANTIGEN.dll 6032703c3efc5f3d3f314a3d42e2a500 \AppData\Roaming\Microsoft\Windows\Recent\cb.exe 12ddf77984d6f2e81a41f164bea12a1c \AppData\Roaming\Microsoft\Windows\Recent\cid.sys 81c9ad6037c14537044b3e54d8b84c99 \AppData\Roaming\Microsoft\Windows\Recent\ddv.exe f28c20c6df79e9fe68b88fb425d36d57 \AppData\Roaming\Microsoft\Windows\Recent\eb.sys 6274e77cd16d6dbec2bb3615ff043694 \AppData\Roaming\Microsoft\Windows\Recent\energy.drv a3342f285bfb581f0a4e786cc90176d2 \AppData\Roaming\Microsoft\Windows\Recent\energy.sys 1ac2fb2dbd0023b54a8f083d9abbf6db \AppData\Roaming\Microsoft\Windows\Recent\exec.exe 2dc3df846ff537b6c3e6d74475a0d03d \AppData\Roaming\Microsoft\Windows\Recent\FW.drv a32f789b1b6f281208fa1c8d54bf8cdc \AppData\Roaming\Microsoft\Windows\Recent\gid.dll b48d1cc8765719a79a9352e2b8f891ef \AppData\Roaming\Microsoft\Windows\Recent\hymt.exe 532c6465f4dd9c7bce31b7a7986e3270 \AppData\Roaming\Microsoft\Windows\Recent\hymt.sys f941f6eedf5b33a0b49b9787d5f0dfc2 \AppData\Roaming\Microsoft\Windows\Recent\kernel32.sys 2ff0c3a804b85d3e7e6487d9bece6416 \AppData\Roaming\Microsoft\Windows\Recent\PE.dll 454f06575c9214f7b9cb01c606fd72fe \AppData\Roaming\Microsoft\Windows\Recent\PE.sys 243b5a8a95bb4f8822790b8f0c81b82a \AppData\Roaming\Microsoft\Windows\Recent\ppal.exe 9d34330ec68d148cc5701d6cd279c84c \AppData\Roaming\Microsoft\Windows\Recent\SICKBOY.drv 493fc17532f9b6ac330dbdb3a01a5361 \AppData\Roaming\Microsoft\Windows\Recent\sld.drv d0d210a62cb66ff452e9a5cfc8e8f354 \AppData\Roaming\Microsoft\Windows\Recent\SM.sys a2ca707ee60338ac5ec964f7685752ba \AppData\Roaming\Microsoft\Windows\Recent\std.dll a1e25ab2f19565f707d85e471f41e08f \AppData\Roaming\Microsoft\Windows\Recent\snl2w.dll
74.125.45.100 4-open-davinci.comUsing bintext to pull the strings from ISe6d_2229.exe provided a few interesting things of note. Specifically a company and product name of "limnol" and file and product version of "1.1.0.1010". Searches for this reference with some added keywords found some additional submissions to virus total but nothing that was not already known from my earlier submission.
74.125.45.100 securitysoftwarepayments.com
74.125.45.100 privatesecuredpayments.com
74.125.45.100 secure.privatesecuredpayments.com
74.125.45.100 getantivirusplusnow.com
74.125.45.100 secure-plus-payments.com
74.125.45.100 www.getantivirusplusnow.com
74.125.45.100 www.secure-plus-payments.com
74.125.45.100 www.getavplusnow.com
74.125.45.100 safebrowsing-cache.google.com
74.125.45.100 urs.microsoft.com
74.125.45.100 www.securesoftwarebill.com
74.125.45.100 secure.paysecuresystem.com
74.125.45.100 paysoftbillsolution.com
74.125.45.100 protected.maxisoftwaremart.com
69.72.252.252 www.google.com
69.72.252.252 google.com
69.72.252.252 www.google.no
69.72.252.252 www.google-analytics.com
69.72.252.252 www.bing.com
69.72.252.252 search.yahoo.com
69.72.252.252 www.youtube.com
There were also strings associated with a Microsoft Windows manifest file. Such a file can be embedded in software by the developer to instruct Windows Vista and Windows 7 on what Privileges the software needs to run as. The default setting of "run as the user" was obtained from the strings:
<security>I continued the analysis by taking a look at the Windows registry. This was done by exporting the HKCU and HKCM hives from the raw image and using both RegRipper and MiTeC Windows Registry Recovery to analyze the entries. The HKCU Run key contained an entry to autostart the executable on startup.
<requestedprivileges>
<requestedexecutionlevel level="asInvoker" uiaccess="false"></requestedexecutionlevel>
</requestedprivileges>
</security>
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run]In addition, I was able to verify that the registry contained an entry for findgala.com under:
"Internet Security Suite"="\"C:\\ProgramData\\e6db66\\ISe6d_2229.exe\" /s /d"
[HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\SearchScopes]The [HKEY_CURRENT_USER\Software\Internet Security Suite] key contained several subkeys within it. The entries here seemed to be similar to the contents of the Instructions.ini file found earlier in the appdata folder of the user profile. This file resided in a hidden folder with the same name as the registry key. I have listed one entry as an example here.
"URL"="http://findgala.com/?&uid=2229&q={searchTerms}"
[HKEY_CURRENT_USER\Software\Internet Security Suite\23071C180E1E]Lastly, the [HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\] key had several entries for what appeared to be legitimate software, tools, and other forms of malware. Entries included; taskmgr.exe, rtvscan.exe (Symantec Endpoint Protection), and dozens of other programs. All legitimate and illegitimate software was being blocked via an entry for debugger with a value of "svchost.exe".
"3016131C2F0B18311F0CF4D5EBEEE1"="4746574B4E544E4D4F4FA0B0B8B2B5BFB7BEA8D9C7"
"23071C180E1E31180D0CE1E6E7"=""
"2205012C0A1F2814131A"="4746574B4E544E4D4F4FA0B0B8B3BDBFB2B7A8D9C7"
"3A160B0D2E090534100CF4F3F7E0F0ECE9E9"="4746574B4E544E4D4F4FA0B0B8B2B5BFB7BEA8D9C7"
"3A160B0D3C1E19192E3BCD"="4746574B4E544E4D4F4FA0B0B8B3BDBFB2B7A8D9C7"
"3A160B0D2F0B181C0A1A"="4746574B4E544E4D4F4FA0B0B8B3BDBFB2B7A8D9C7"
"3A160B0D34140E101F13D5F1E6E2F0E0"="4746574B4E544E4D4F4FA0B0B8B2B5BFB7BEA8D9C7"
"3E22081D1B0F19"="46"
"24181415181A1F16"=""
"2205012C0A1F1D091B2DF5EFC1ECF1EBF2"="46"
"3E1E1C1D1F15290D1A1EF4E4C1ECF1EBF2"="46"
"3B1E0A0B15093F120B11F4"="46"
"3218151813154C"=""
"23071C180E1E"="46"
Dynamic Analysis
I began dynamic analysis by first attempting to infect a virtualized Windows 7 system in my lab (Note: all initial attempts were with administrator privileges with UAC disabled). Running the executable seemed to generate a runtime error, so I attempted to run it from the command prompt with the /hkd switch found in the desktop shortcut during static analysis. Process Monitor was used in an attempt to capture all file, registry, and network connection changes during infection. The following error was displayed;
Thinking it picked up on Process Monitor, I tried again but without procmon.exe but I was presented with the same error. It seemed that this sample was VM aware. Again I attempted to infect a clean install of Windows 7 on physical hardware with procmon.exe and again, I was met with failure. I turned to utilizing CaptureBat to monitor file and registry changes during install. Infection proceeded but I noted my sample used for analysis had been removed. On further inspection, it appeared that a .bat file was the culprit. The contents of the file were as follows;
MD5 FileNameI also noted the name of the files and folders associated with the malware seem to vary on each infection. Verification of hashes proved that it was indeed the same malicious program however. File and registry monitoring verified the findings from the static analysis and I noted some additional changes as well. It appeared the rogue software attempts to disable UAC by editing the following registry keys;
329e8a313f20cd8b4ebf67642331c007 \Users\bugbear\AppData\Local\Temp\del.bat
:Repeat
del "C:\Users\bugbear\Desktop\e6db66\ISE6D_~1.EXE"
if exist "C:\Users\bugbear\Desktop\e6db66\ISE6D_~1.EXE" goto Repeat
del "C:\Users\bugbear\AppData\Local\Temp\del.bat"
registry: SetValueKey C:\Users\bugbear\Desktop\e6db66\ISe6d_2229.exe -> HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System\ConsentPromptBehaviorAdminAdditional registry entries in HKEY_Current_User were also modified. Including the Internet Explorer proxy and wpad settings under [HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings]. Additionally, rather than modify the host file directly, the executable seemed to create a temporary host file, remove the old one, and replace it with this new version.
registry: SetValueKey C:\Users\bugbear\Desktop\e6db66\ISe6d_2229.exe -> HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System\ConsentPromptBehaviorUser
registry: SetValueKey C:\Users\bugbear\Desktop\e6db66\ISe6d_2229.exe -> HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System\EnableLUA
file: Write C:\Users\bugbear\Desktop\e6db66\ISe6d_2229.exe -> C:\Windows\System32\drivers\etc\host_newTypical "features" associated with scareware seemed to be included with this sample. The rogue software begins a "scan" of the infected system immediately upon execution. Scan results display "infected" files located in [root]\Users\%username%\AppData\Roaming\Microsoft\Windows\Recent\ folder identified during static analysis.
file: Delete C:\Users\bugbear\Desktop\e6db66\ISe6d_2229.exe -> C:\Windows\System32\drivers\etc\hosts
file: Write C:\Users\bugbear\Desktop\e6db66\ISe6d_2229.exe -> C:\Windows\System32\drivers\etc\hosts
file: Delete C:\Users\bugbear\Desktop\e6db66\ISe6d_2229.exe -> C:\Windows\System32\drivers\etc\host_new
Please note, no attempt was made to identify these files as legitimate malware by myself, although that may be an interesting exercise for another time. Not unlike an episode of the Soprano's, the victim is intimidated into buying protection and is offered several opportunities to buy a subscription. Multiple subscription options are available.
At one point my lab system spewed a blood curdling scream from its speakers before displaying yet another option to "protect" oneself (a little over the top if you ask me). My favorite feature goes to Chat Support however.
I do not think Jane appreciated my bluntness. Network connections for both the subscription service and chat support sessions were collected with the following script which leverages the netstat command.
for /L %1 in (0,0,0) do netstat -anob>>C:\netstat.txtBoth IP addresses associated with the subscription service and chat support sessions were registered to hosting providers here in the US. The strangest behavior observed however, was captured with Process Explorer and Wireshark post infection. Multiple instances of ping.exe running under cmd.exe were noted. Upon examination of the packet capture, it appeared the processes were spewing ICMP and SYN packets to two IP Addresses registered to .RU domains.
Soon after this behavor was noted. The executable associated with the infection was mysteriously removed from the system. Attempts to duplicate this behavior later failed.
Further analysis of the infection and sample was done without administrator rights and with UAC disabled. No edit of the hosts file or registry keys in HKLM were noted, however. The malware still setup shop within the ProgramData and User Profile locations noted with the earlier analysis but the fact the user with the original infection had no administrator rights and the host file and HKLM keys were modified remains a bit of a mystery. One might speculate, the original payload might behave differently.
Further Google searching utilizing these findings led me to Microsoft's Malware Protecton Center write-up on Rogue:Win32/FakeVimes. Although Virus Total had not indicated such, it would seem our sample has had many aliases and upgrades.
Lessons Learned
All in all I learned a lot and had fun analyzing the sample (it beats watching sitcoms). Few things I noted for future analysis attempts.
- Always verify your images and keep the original copy if possible (aka don't be a dumbass Tim)
- Static file forensics techniques can be very useful during malware analysis
- Have multiple tools that can perform similar tasks is sometimes needed
- Fear is a powerful marketing angle and the bad guys are getting better at it
Feel free to ping me if you would like a copy of the sample. I would be more than happy to trade notes with others.
Update: Questions Unanswered
Updated on December 30, 2010.
Curt Wilson was kind enough to comment on my analysis earlier this week. He brought up an interesting tidbit that I had missed. The title of error message displayed when attempting to perform dynamic analysis in a virtualized environment references Themida, a known packer used in malware. The following screen shot obtained from Google images is telling:
According to the results of my initial Google searches, Themida has been around for some time. There are some scripts available for OllyDbg to unpack executables using this tech so I hope to continue down the rabbit hole.
Moreover, I think the files placed in the recent folder of the user profile is worth a quick look, as is the payloads of packet captures. Looks like I have some interesting commutes ahead of me on the train. Until Part II of the analysis, Happy Hunting!
Subscribe to:
Comments (Atom)