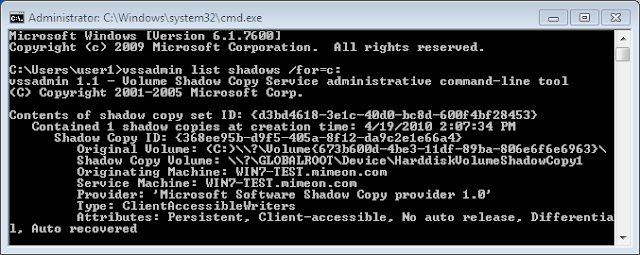
Vssadmin is a command line tool that can be used to display current VSS backups. To do so, use the syntax;
vssadmin list shadows /for=c: (where c: is the volume your working with).Here is an example of the output;
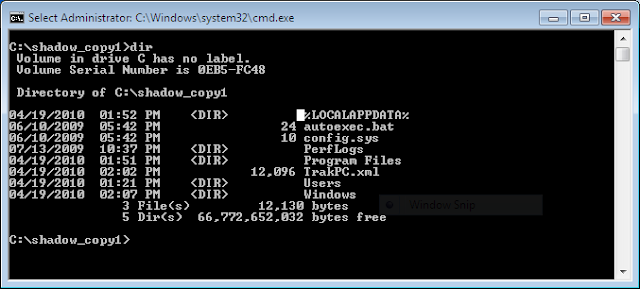
Make sure to note the Shadow Copy Volume you want to analyze and use it with Mklink to create a symbolic link to the backup. For example;
mklink /d C:\shadow_copy1 \\?\GLOBALROOT\Device\HarddiskVolumeShadowCopy1\ (note: the trailing back slash as it is needed).Once created you can browse the symbolic link as you would any folder and restore files of interest by copying them out.
Happy Hunting.
References:
MSDN Blog: A Simple Way to Access Shadow Copies in Vista
Updated June 10, 2011
I came across a great post from @4n6woman on using Log Parser to parse mounted VSC's and preserve the MD5 HAshes and Metadata for easy querying. Thought I would share.
No comments:
Post a Comment